by Guillermo J. Rosas, Faculty, Information Technology, Metropolitan Community College
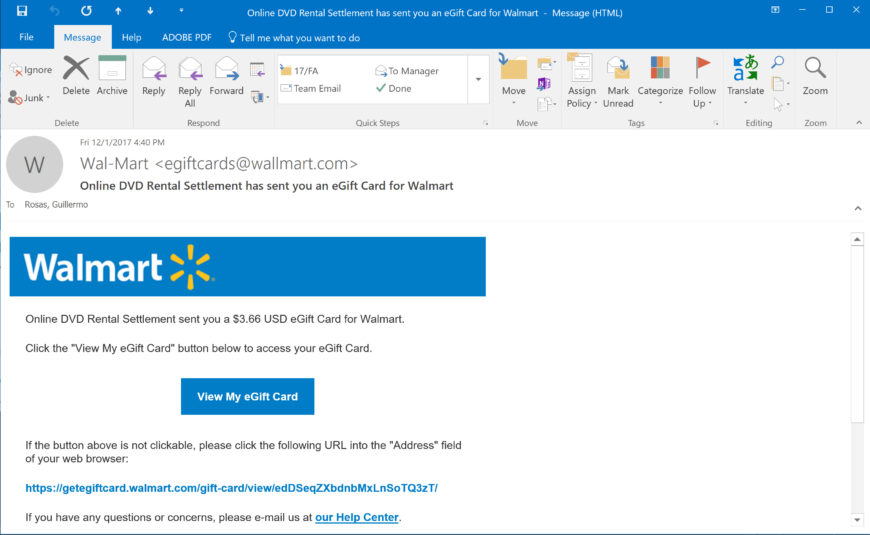
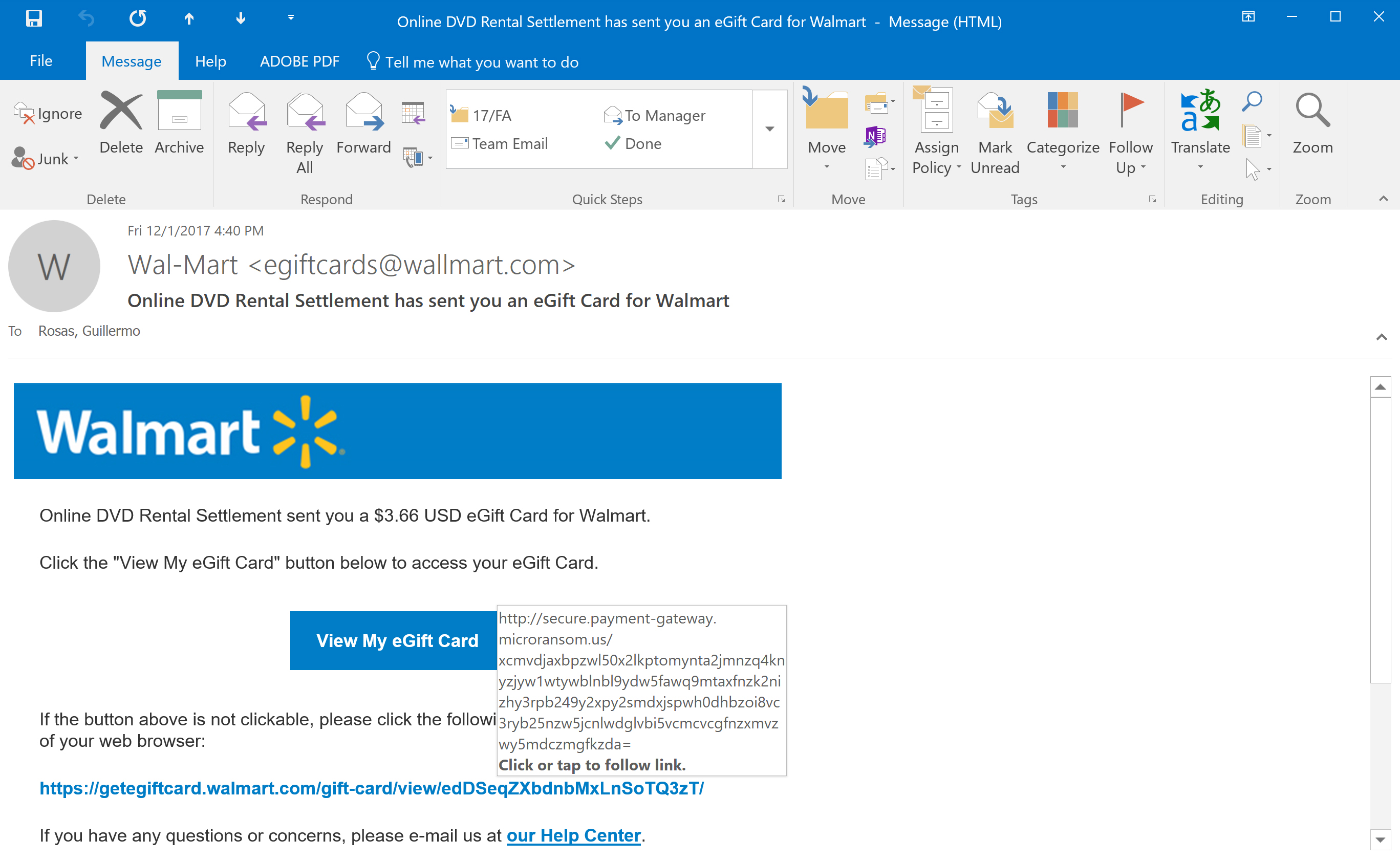
As faculty, we’re always receiving SPAM email of one sort or another; however, this evening I received an email from “Wallmart” informing me I was the recipient of a generous $3.66 eGift Card for Walmart as part of an “Online DVD Rental Settlement” (Figure 1).
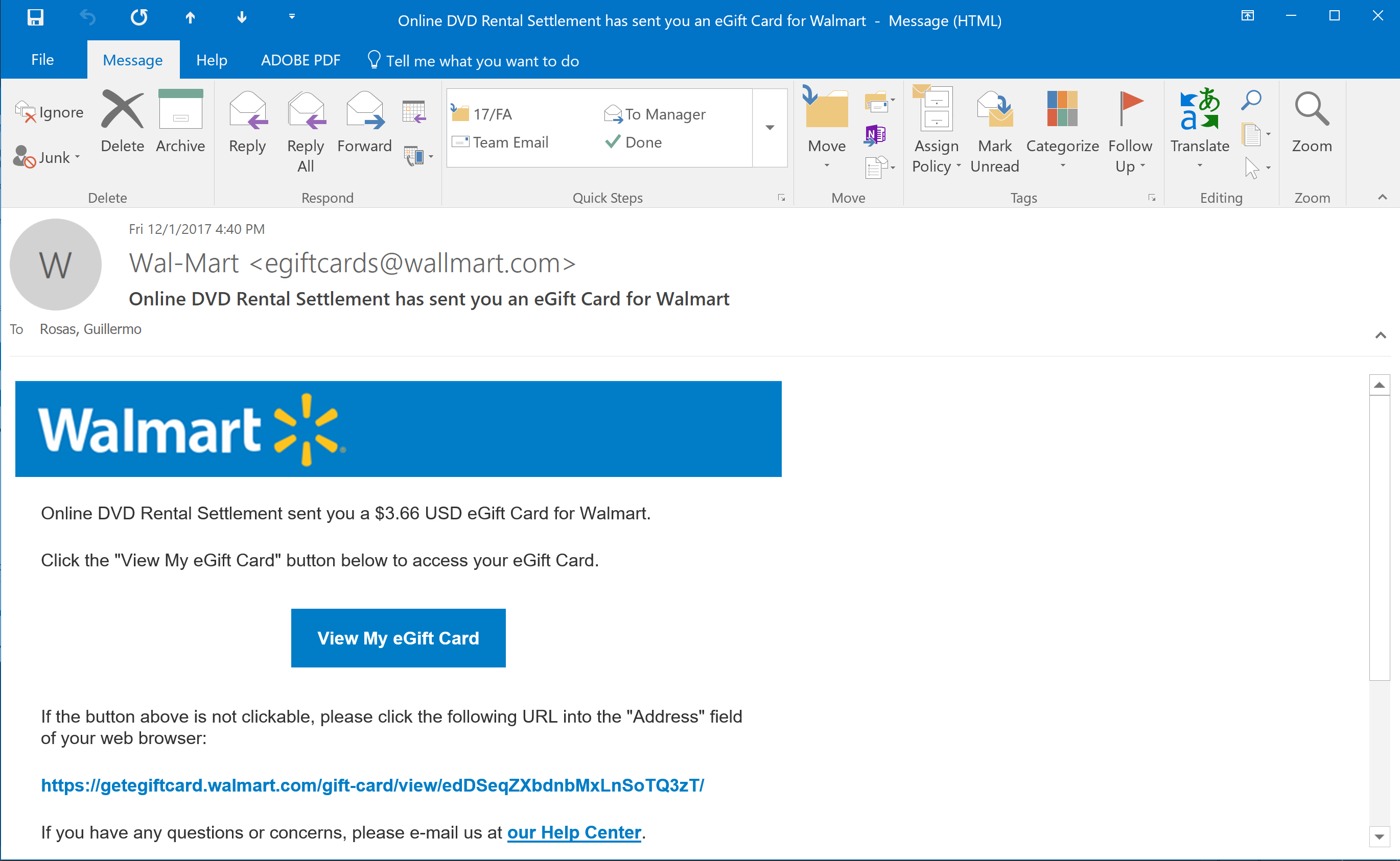
I hope you notice the fact that I surrounded “Wallmart” in quotation marks in my previous paragraph. Let’s take a closer look at this email (Figure 2). Notice how the email is coming from egiftcards@wallmart.com – did you catch that second “L” in the sender’s email domain? It’s interesting because Walmart is spelled with one “L.” The sender includes a Walmart logo at the top of the email – note how the logo is spelled correctly, with one “L.” Although Figure 2 doesn’t point it out, the subject of the email also spells Walmart correctly, with the single “L” – the sender’s domain is the only item that is “misspelled” in this email.
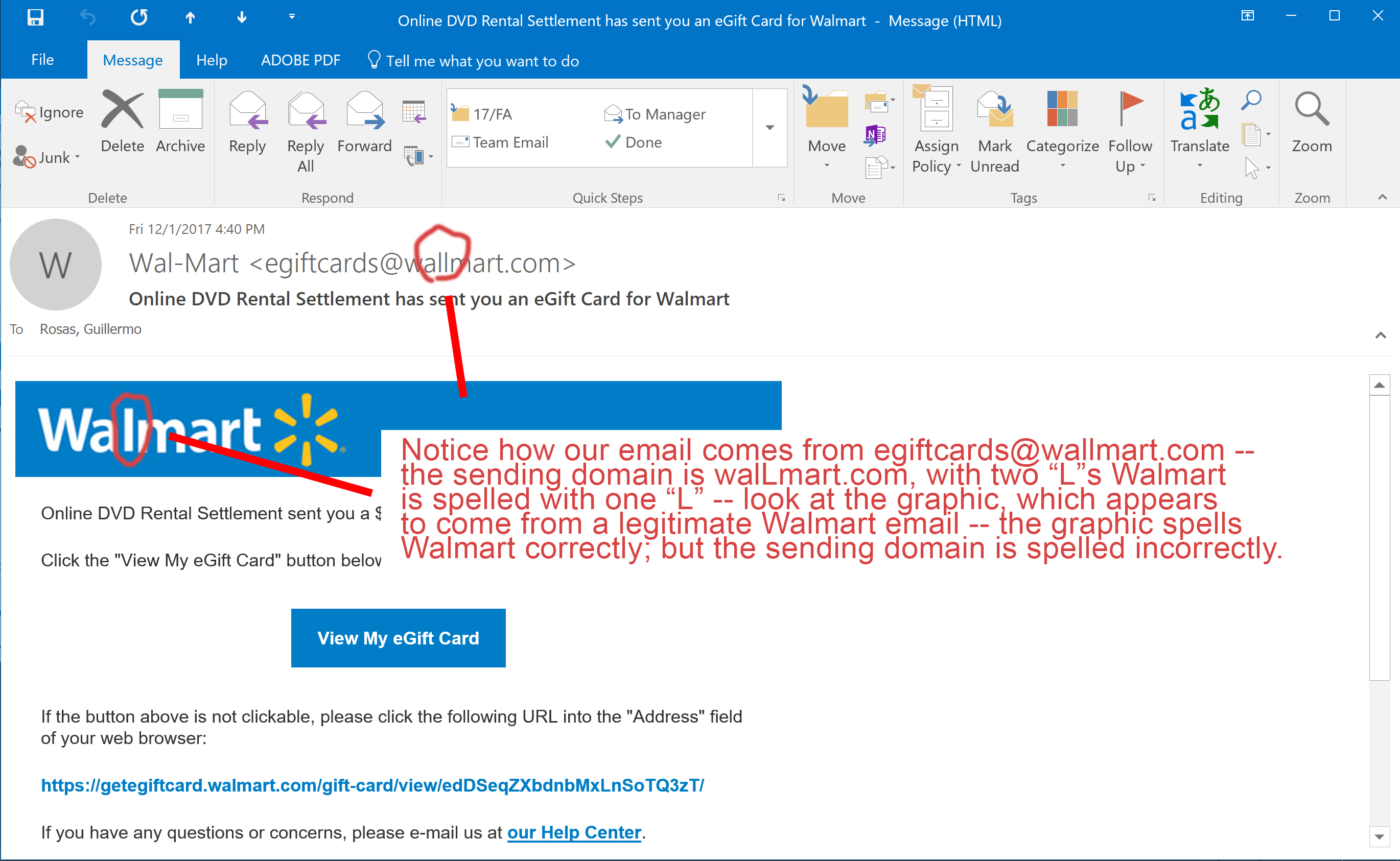
These are red flags. Why would I be receiving an email from Walmart from a sending domain of “Wallmart.com”?
Interesting. Let’s not click on anything, though. Microsoft Outlook will display the linked URL when we hover our mouse over a hyperlink. Let’s use this feature to find out a little more about our email.
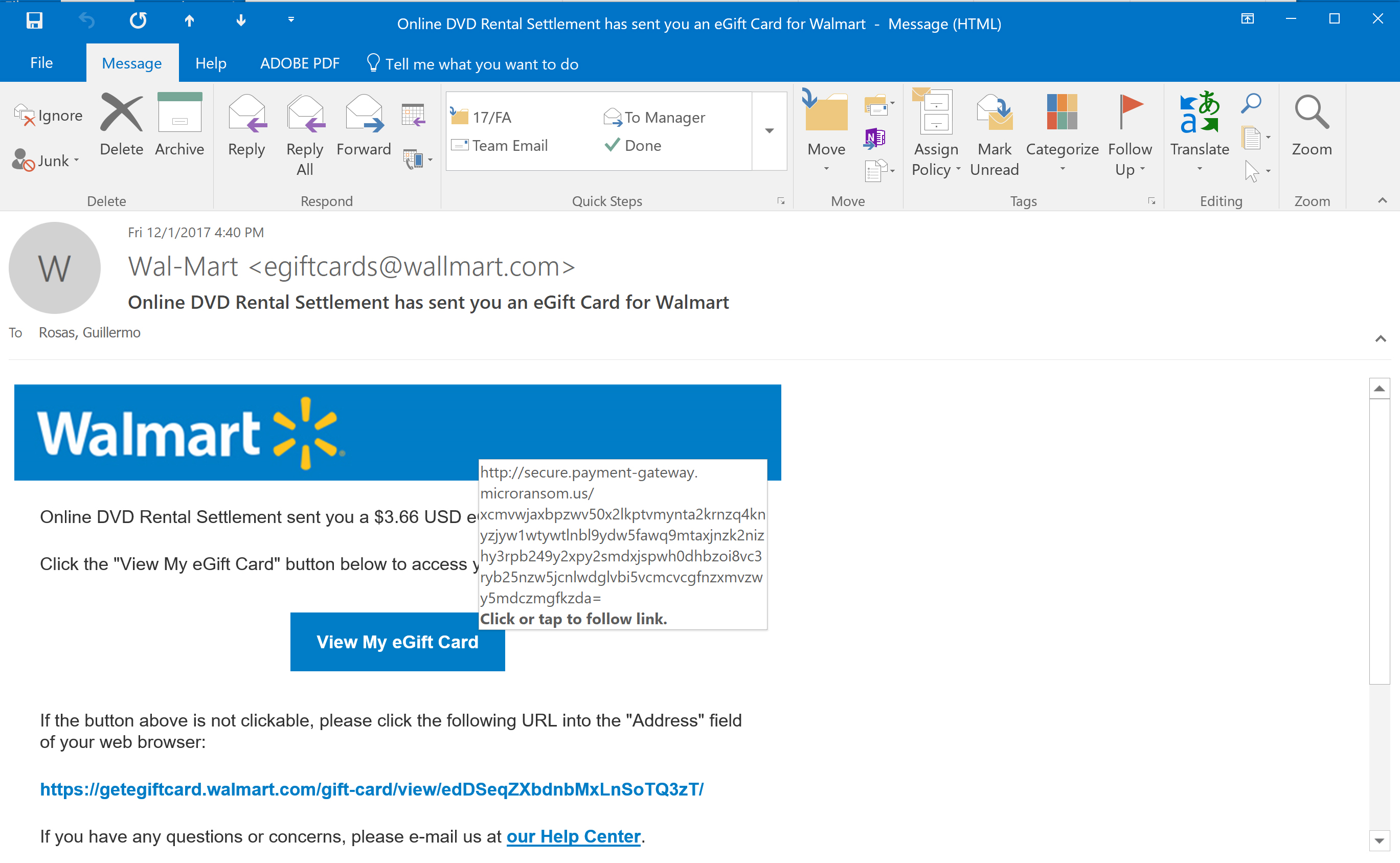
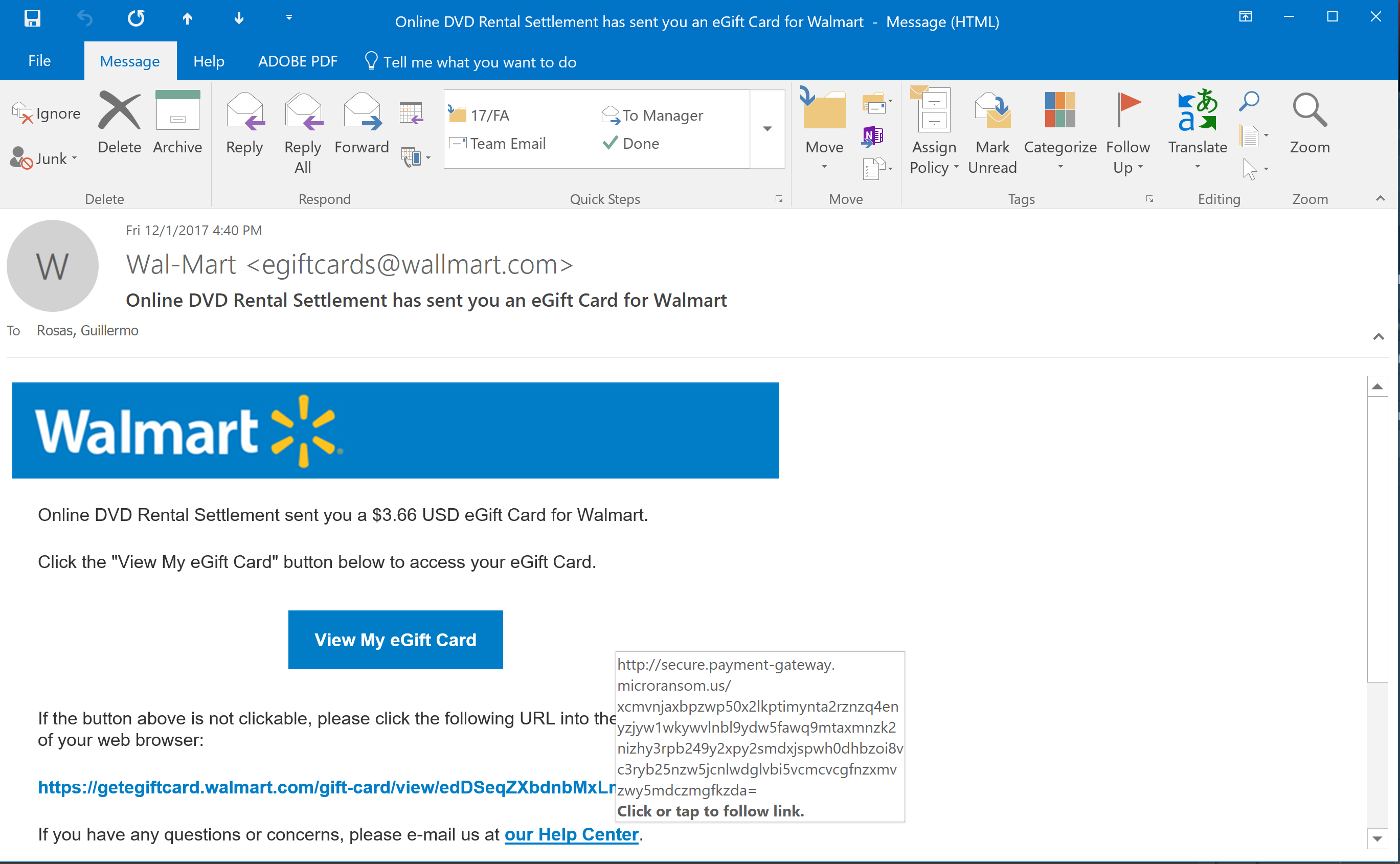
When I hover my cursor over the button, View My eGift Card, a popup appears (Figure 3). Note the URL that appears in the label that appears - secure.payment-gatteway.microransom.us – doesn’t sound like a Walmart-type website. It also doesn’t sound like a very nice URL to visit.
Let’s hover over the URL at the bottom of the page, the text of which says it will take us to, getegiftcard.walmart.com – that’s sounds legit. Plus I want my $3.66
Placing my mouse over the getegiftcard.walmart.com link shows the linked text will actually take us to secure.payment-gateway.microransom.us — it’s not looking as though I’m going to get my $3.66 any time soon 🙁
Grrrr… I want my $3.66. Let me check that Help Center link at the bottom of the page. I hover my mouse of the text our Help Center and the linked URL appears…. and it also leads to secure.payment-gateway.microransom.us … alas, it doesn’t look like I’m going to get my $3.66 eGift Card… oh the things I could buy with that.
So what do I do now? Panic? That’s usually fun, but it’s not really a good option. The solution to this is simple:
- Always be skeptical about the links in any email message; don’t just click on a link, even if it comes in an email from a person you know.
- If you are tempted to click on a link, or if you have to click on a link, examine the link to make sure it’s going to direct you to where it says it’s going to direct you. In this example, the link looks like it’s going to take us to a Walmart.com-hosted resource, but when we examine the link, we see we’re actually going to get taken to a resource hosted on a site named microransom.us
- If you receive a suspicious email from someone you know (a student, a teacher), call that person or go visit them and ask them if they sent the email. Email can be spoofed and it may look like someone you know is sending an email with a malicious link.
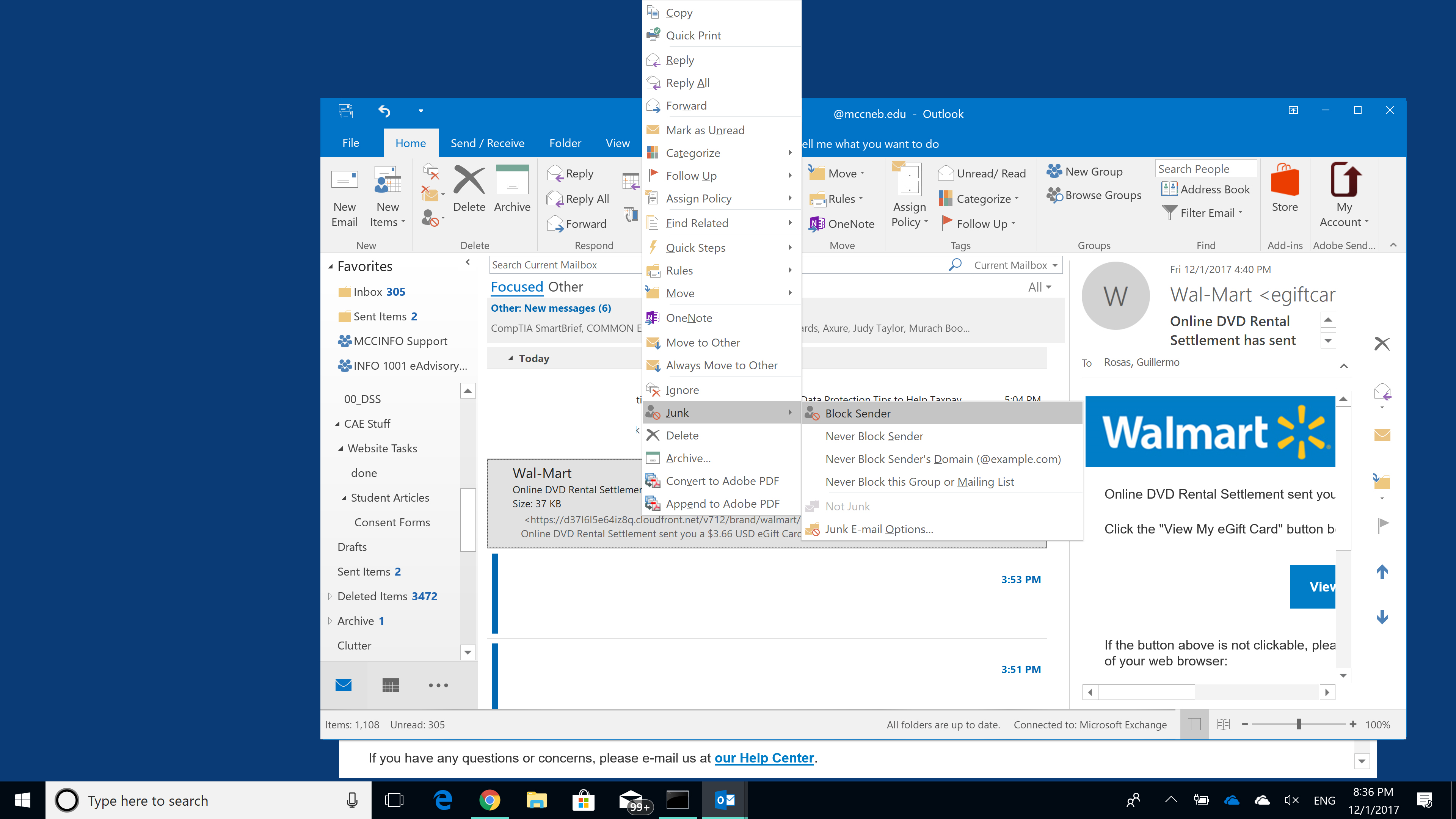
- If you receive an external email from someone like Walmart (as shown in this article), simple mark the email as Junk/SPAM – this will help your email software’s filters learn what emails are unwanted. In Microsoft Outlook (desktop and webapp), you can mark an email as Junk by right-clicking (CTRL+Click in macOS) and then clicking Junk > Block Sender
With the holidays right around the corner, we’ll probably see more emails like these in our MCC inboxes. Generally, there’s nothing to worry about – criminals cast wide nets hoping to catch a few people. Don’t be one of the few – act smart, be suspicious, and don’t fall for scams.

Guillermo J. Rosas is a full-time faculty member in the Business and Information Technology Department at Metropolitan Community College (MCC). He has over 18 years of experience in the field of Information Technology. Prior to joining MCC’s faculty, Guillermo worked as a Network Defense technician at the USSTRATCOM Network Operations Center.
Guillermo holds a BS in Information Systems from Bellevue University, and a MBA from Bellevue University. His professional certifications include: A+, Security+, Network+, Linux+, Certified Ethical Hacker, and Certified Information System Security Professional (CISSP).