Contributed by Glenn Flenorl, Cybersecurity Major
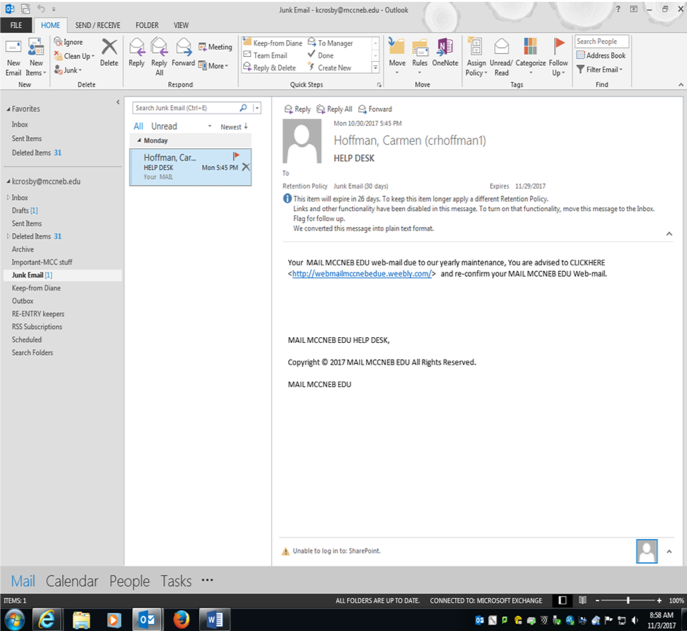
In Today’s world of technology and learning, the threat of someone misusing technology is always present. Recently, there have been a rash of bogus emails going around the school as seen below (Figure 1). This is called Phishing.
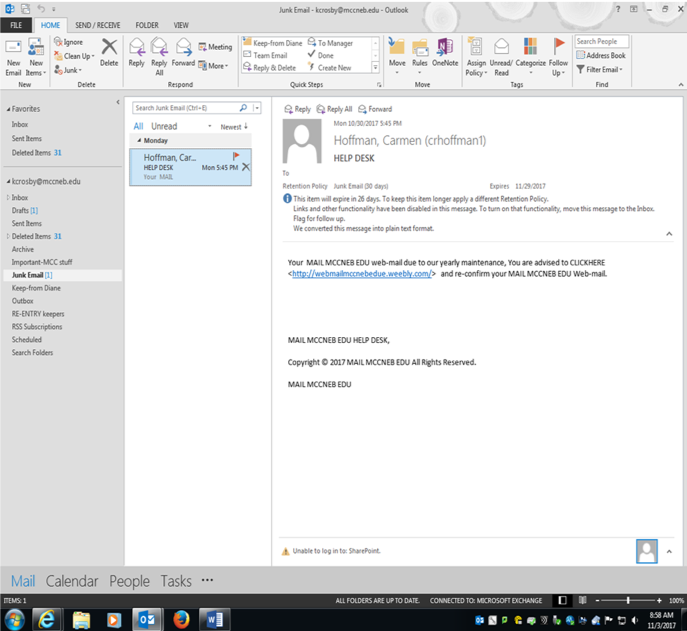
What is a phishing attack? Phishing is a type of social engineering attack often used to steal user data, including login credentials and credit card numbers. It occurs when an attacker, masquerading as a trusted entity, dupes a victim into opening an email, instant message, or text message ( google 2017). This is a example of what been going around the campus. As We take a closer look at the email it looks all normal. That’s what its suppose to do look normal. Then we look at the name now since I’m a student here I got to thinking to verify things I looked up the name. There is a number of things faculty and staff to do if they get something that looks bogus or untrustworthy. Simple ask your co-workers, look up the name like I did in the school staff dircetory. That was evdince for me to say this is not real and I told co-workers and students right away. And the school always sends out help deck emails with no link in in its been standard protocol here at the college that the HELP DESK does not put links in the emails. So it is good practices to always be sure of the email that is being sent to you is by the party the is familiar.  Step one is to go to the MCC My WAY site click Menu (Figure 2).
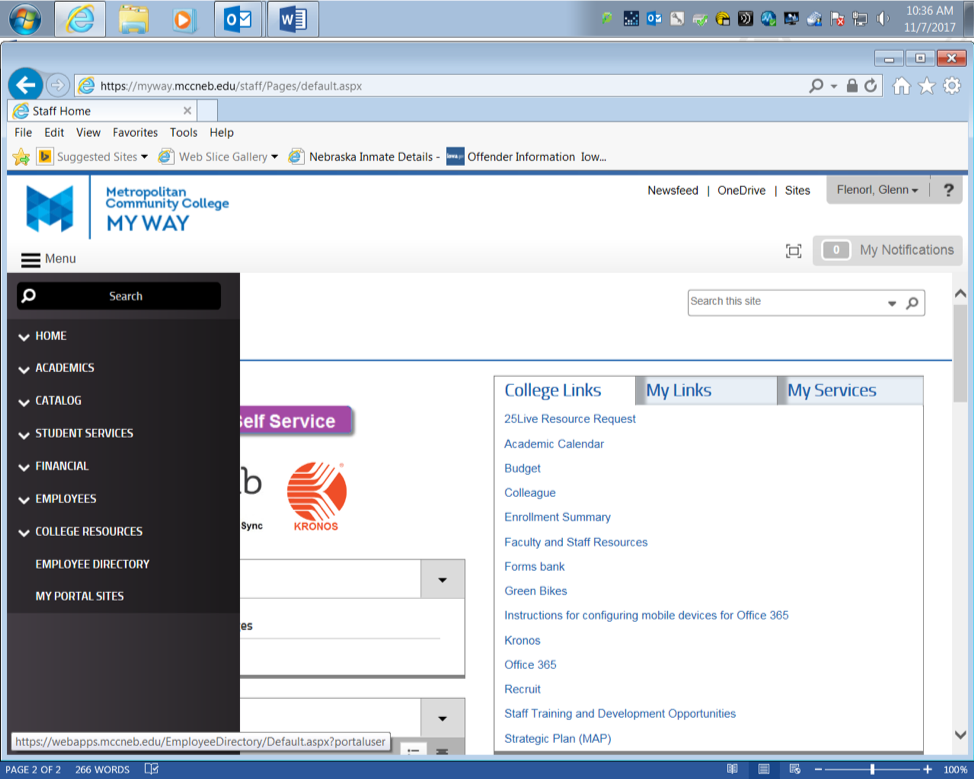
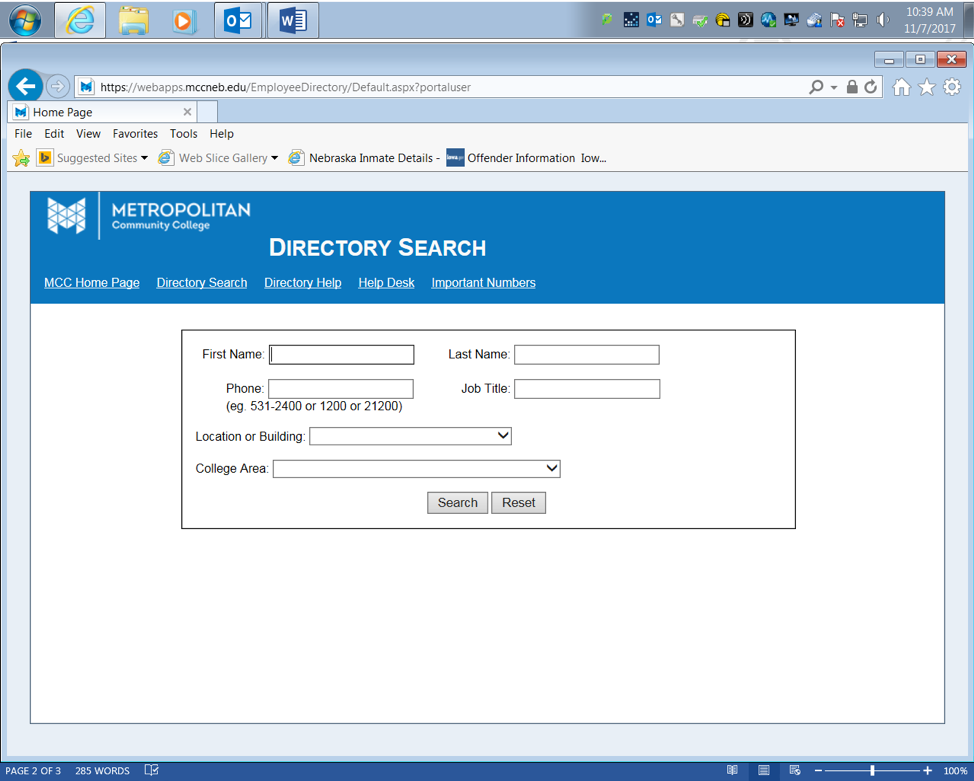
Second go to the employee directory (Figure 3). In the drop down menu got to help desk to get yourself armed with knowledge to better combat phishing attempts by knowing who is in the help desk department and or building location.
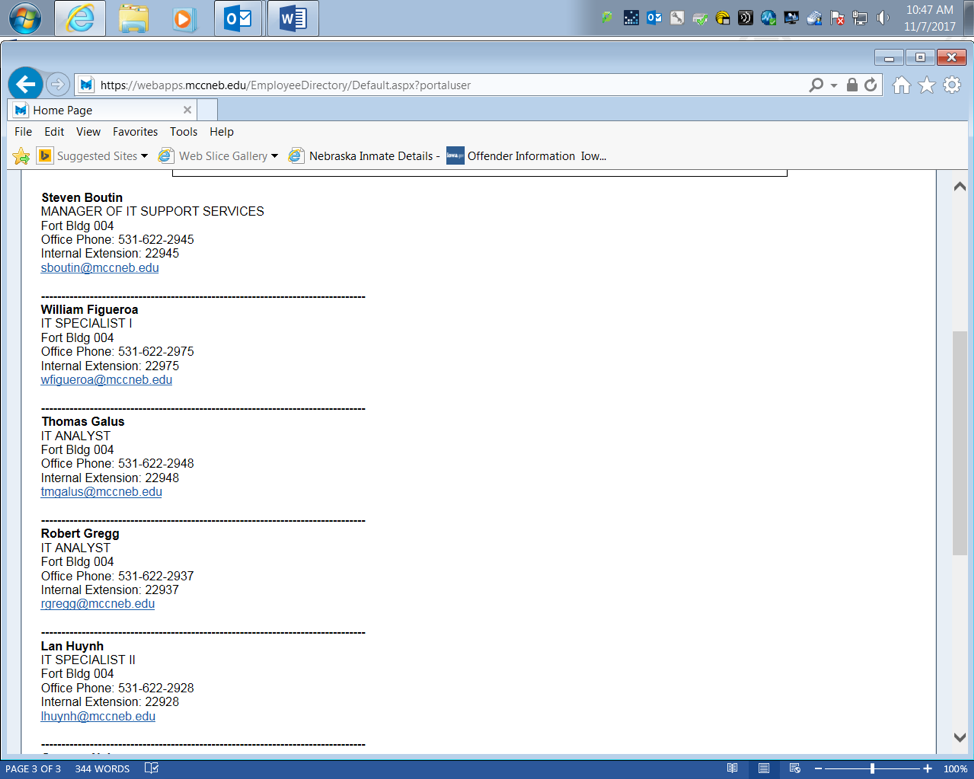
I just happen to know building 4 is where IT HELP DESK is here on Fort campus an as you can see there is no Hoffman anywhere (Figure 4).
Just by knowing who is in an around the technology can better prepare us as learners and as staff to not get dupped into bogus email opening.
My name is Glenn and I’m an Information Technology Assurance Transfer. I work at MCC’s 180-Re-entry assistance program as a peer-mentor. A former office mate (Lyndsie Gibbs) encouraged me jump back into INFO SCI. and I really enjoy the learning and using the new technology available.


 My name is Matt Reida, and I am pursing an associates degree in Server Administration at Metropolitan Community College. As a very young child, I was enamored with computers, and strived to learn about them constantly. As I grew older, my passion for learning remained, and inspired me to pursue a career in the IT field.
My name is Matt Reida, and I am pursing an associates degree in Server Administration at Metropolitan Community College. As a very young child, I was enamored with computers, and strived to learn about them constantly. As I grew older, my passion for learning remained, and inspired me to pursue a career in the IT field.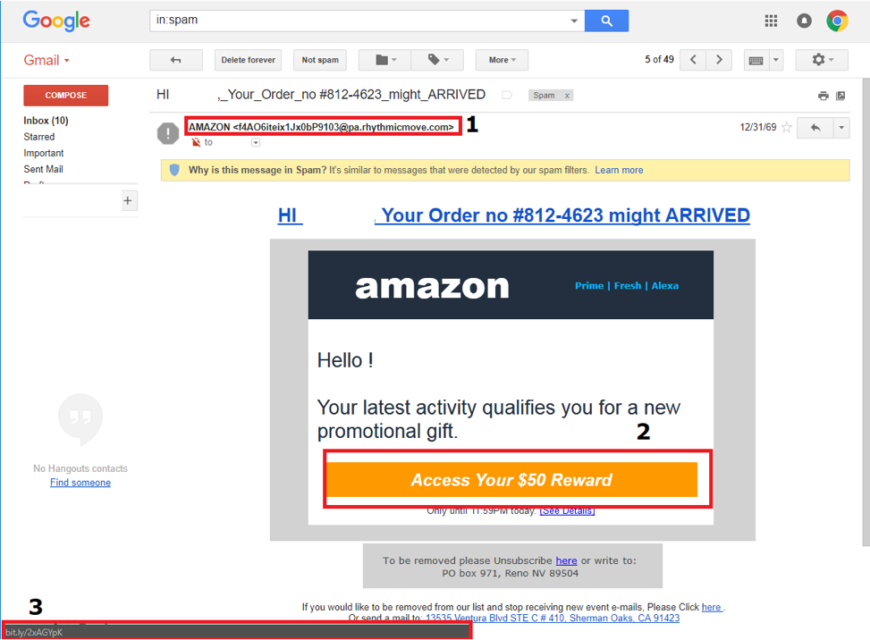
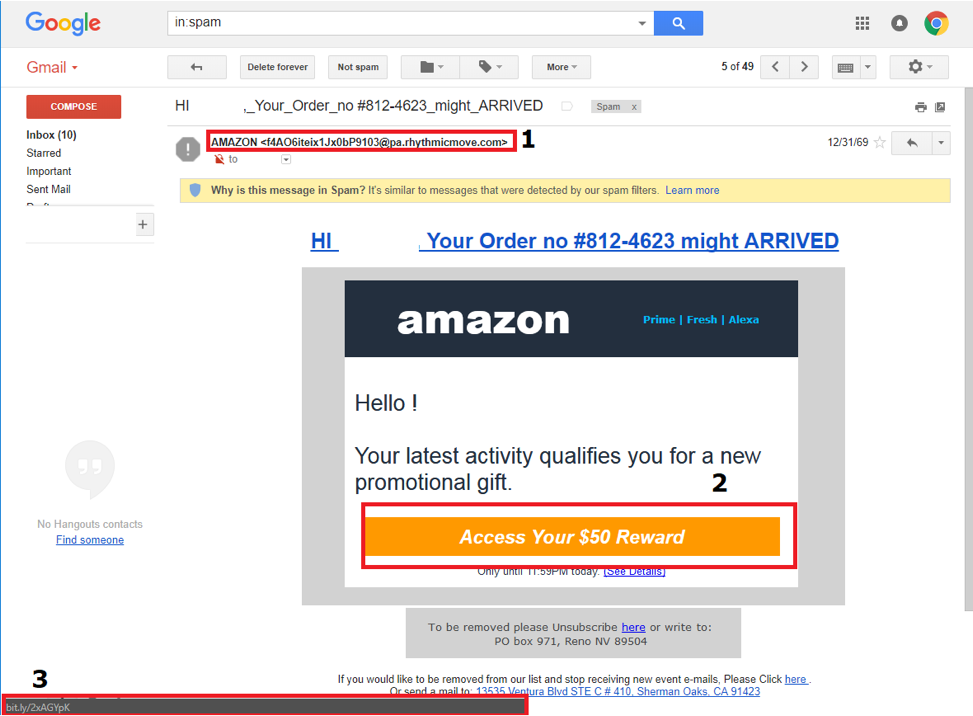 Highlighted in the red boxes are indicators that alert me to this email is in fact a phishing attempt. Although the email says it is from Amazon, 1st red box, we can tell upon further inspection that it is not from Amazon. Looking at the email address of the sender and ensuring that it is from the actual website itself and not a suspicious chunk of text is the first red flag. Going onto the 2nd red box we can see that I’m entitled to a $50.00 reward for my latest activity. This however is the bait to entice me to clicking the link that will either install malicious software on my computer (malware) or direct me to a website that is designed to appear just as Amazon’s login page looks like and steal my personal information. Upon hovering over the link with the cursor we can see 3rd red box which is a URL shortener. Amazon does not use these and being aware of where links are directing the user to is important. The key part in this is identifying the web address. Some phishing emails attempt to mask the address as such:Â
Highlighted in the red boxes are indicators that alert me to this email is in fact a phishing attempt. Although the email says it is from Amazon, 1st red box, we can tell upon further inspection that it is not from Amazon. Looking at the email address of the sender and ensuring that it is from the actual website itself and not a suspicious chunk of text is the first red flag. Going onto the 2nd red box we can see that I’m entitled to a $50.00 reward for my latest activity. This however is the bait to entice me to clicking the link that will either install malicious software on my computer (malware) or direct me to a website that is designed to appear just as Amazon’s login page looks like and steal my personal information. Upon hovering over the link with the cursor we can see 3rd red box which is a URL shortener. Amazon does not use these and being aware of where links are directing the user to is important. The key part in this is identifying the web address. Some phishing emails attempt to mask the address as such: 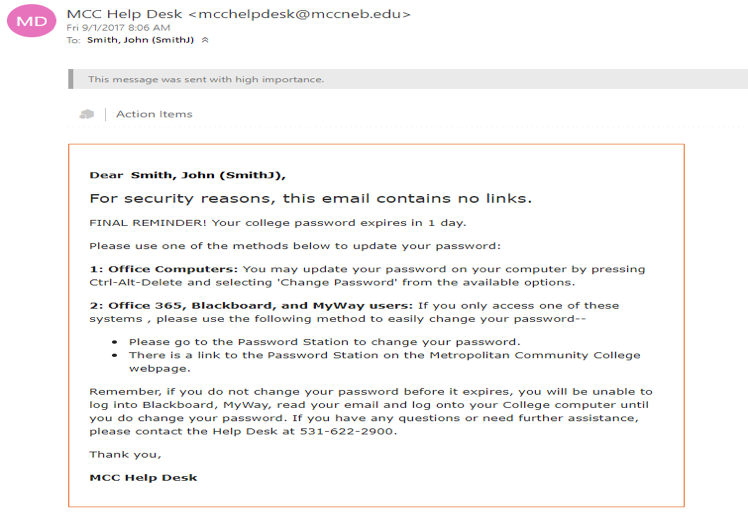
 Christopher Wagner is a computer enthusiast and enjoys learning about InfoSec. At age 10 he was given his first computer and that sparked a growing passion in learning how they worked. In addition, he found an interest in the ever-evolving world of InfoSec. What started as simple viruses to annoy people to ransomware demanding payment in return for decrypting data. Learning how to build computers and troubleshoot issues that arose, he was able to start freelancing computer repair. Most recently, Christopher started attending Metropolitan Community College for Information Assurance and hopes to one day find a career in InfoSec.
Christopher Wagner is a computer enthusiast and enjoys learning about InfoSec. At age 10 he was given his first computer and that sparked a growing passion in learning how they worked. In addition, he found an interest in the ever-evolving world of InfoSec. What started as simple viruses to annoy people to ransomware demanding payment in return for decrypting data. Learning how to build computers and troubleshoot issues that arose, he was able to start freelancing computer repair. Most recently, Christopher started attending Metropolitan Community College for Information Assurance and hopes to one day find a career in InfoSec.